(DES) known as Data Encryption Standard is a very old and outdated method of encrypting data using symmetric key method. This method was actually adopted in the year 1977, particularly to secure the confidential data of government agencies. The method of data encryption was made obsolete in the year 2005.
Historically speaking, researchers from IBM had originally designed this encryption standard in the early part of 1970s. Later it was adopted by U.S National Bureau of Standards (this is now known as the National Institute of Standards and Technology) and implemented as FIPS – Federal Information Processing Standard in the year 1977. The objective was to encrypt commercial, sensitive, and classified data of the government.
This encryption was the first one that the U.S government had approved for public usage. As soon as this decision was made, industries such as the financial services sector started adopting this encryption method. Since Data Encryption Standard was a simple encryption method, it was used in a variety of embedded systems such as:
- Smart cards
- SIM cards
- Routers
- Modems
How does DES work?
Data Encryption Standard uses a single key for encrypting and decrypting a message. This means that the sender and receiver both must have the same key to access the message. At one point in time, DES was the go-to encryption technology. However, over a period, DES was overpowered by the more sophisticated AES (Advanced Encryption Standard).
Here are some of the important features that impact the working of the Data Encryption Standard.
Block cipher This means that the entire Data Encryption Standard is a cryptographic key, which is applied to a block of data and not on a single bit. For instance, to encrypt a plain text message, DES will put the message into blocks of 64 bits and then encrypt it.
Multiple rounds of encryption The DES methodology is a process of encryption that is done 16 times. This is done in four different modes, by encrypting blocks individually or creating a relationship of each cipher block with all previous blocks. Decryption is just the opposite of encryption, where you must follow the same steps but in reverse order.
64-bit Key DES actually uses a 64-bit key, however, eight of those bits are utilized for checks making the effective length to only 56 bits. The algorithm for encryption products 16 different subkeys of 48 bits each. Each of these subkeys is used for 16 encryption rounds.
Replacement & Permutation The algorithm also helps in defining the sequence of replacement and permutation that the cipher undergoes during the process of encryption.
Backward Compatibility DES also provides this compatibility in some cases.
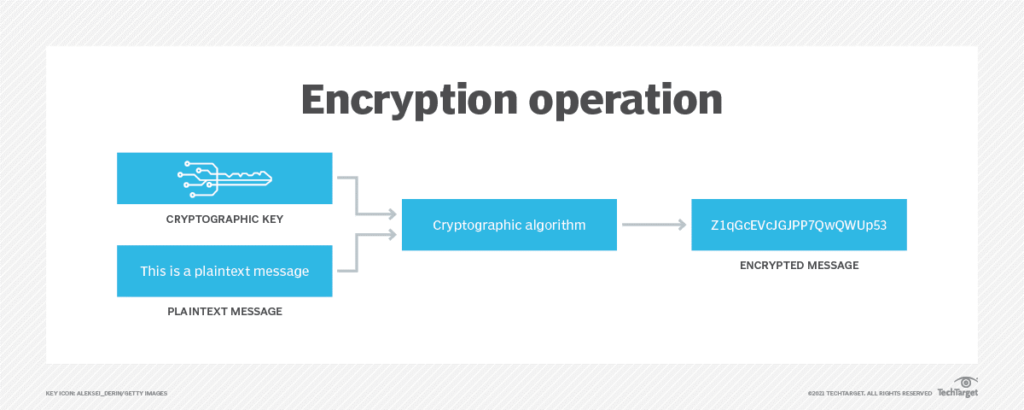
The following diagram explains how encryption converts a plain text message into an encrypted message
Source: https://searchsecurity.techtarget.com/definition/Data-Encryption-Standard
Implementation and testing of DES
To implement DES the fundamental requirement is a security provider. Though there are a plethora of service providers available to select from, it is important to select the right one. One criterion for selecting the security provider is the knowledge of languages such as Java, Python, C, or MATLAB.
Once a service provider is selected, then the next step is to choose a random secret key. This will be executed by the Key Generator, or one can create on their own.
Subsequently, it is important to test the encryption that is created. This is to check for any vulnerability and ensuring that it is properly implemented.
Why is Data Encryption Standard not safe?
For any encrypted cipher, the fundamental method of attack is force. This involves trying each key until you hit the one that is the right one. Length of the key determines the possibilities, and thus the possibility of easy attack.
DES encryption comes with a key length of 56 bits. If you make a probability, then the possibility of breaking the encryption and finding the key is 72 quadrillion times. This is not enough considering the power of modern computers and the technology used today. There were many experts who were of the opinion `that the 56-bit length of the encryption key was not sufficient enough even before Data Encryption Standard was adopted as a standard. It was always suspected that constant interference by National Security Agency caused significant interruptions in the original algorithm rendering it weaker.
DES vs AES
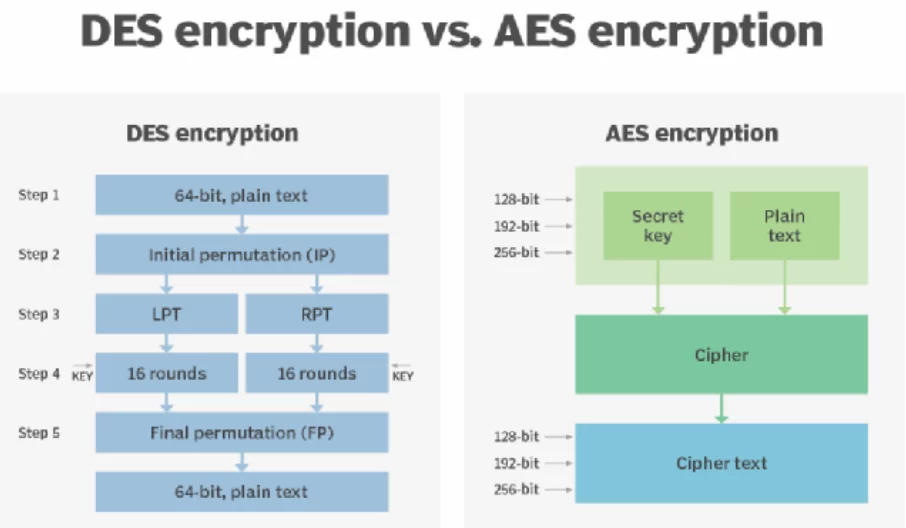
We know that strength of encryption is directly proportional to the length of the encryption key. Considering the processing power of modern computers, 56-bit key lengths are very small. As a result, in 1997, the National Institute of Standards and Technology (NIST) decided to select a successor to DES and started an evaluation period that lasted for 5 years, comprising 15 different algorithm programs. Finally, in the year 2001, NIST shortlisted Rijndael cipher. After undergoing some modifications and tweaks, it became the modern-day AES. The following diagram gives a comparative view of DES and AES.
Source: https://searchsecurity.techtarget.com/definition/Data-Encryption-Standard
Current usage of Data Encryption Standard
Even though both DES and 3DES algorithms are completely obsolete purely due to their key length, we can still find some utility of these algorithms. However, the usage of this standard comes with a disclaimer that the users must understand the potential risks involved in using this standard. And the risk will keep growing the more you use it.
Today, Data Encryption Standard is not used for encrypting any kind of confidential data. However, DES and 3DES are still used in a limited capacity for providing training on cryptography. Today, Data Encryption Standard and all its variants are used for coaching on cryptography. In this training, a detailed understanding of the algorithm is provided. Furthermore, detailed research on the functioning and effectiveness of DES encryption is imparted and so is the method of how to effectively attack it. The technology is purely used for academic purposes to showcase the fundamentals of digital cryptography, encompassing:
- Permutation and replacement of ciphertexts
- Techniques on how to apply keys and how to find them
- Finding out loopholes in cryptographic algorithms
Why learn DES, if irrelevant?
In spite of DES becoming redundant, it is important to learn this algorithm. When it comes to the subject of cryptography, the relevance of the DES algorithm will always hold a stand. The reason being the DES algorithm was the foundation of all subsequent algorithms for encryption. Once the origin of data encryption is understood, then it becomes easy to understand the fundamentals of modern-day encryption methods. Hence, it is important to learn DES encryption and get clarity on its fundamentals.
What is the legacy of DES?
Even though DES went completely obsolete from a commercial usage point of view, it does serve the purpose from an academic standpoint to propagate the learning of cryptography and even create new algorithms. Until DES came into existence, cryptography was confined to military and government intelligence organizations only.
The nature of DES is quite open, which means that anyone who is interested in mathematics, academics, or data security was able to study the operation of this algorithm and crack it. Just like any puzzle creates a frenzy, this one created an entire industry.
Final Thoughts
Cryptography is a method that is deployed to create communication in a secure mode. In yesteryears, some of the most commonly used methods were DES and 3DES. Today we see AES being used as the standard for encryption.